摘要
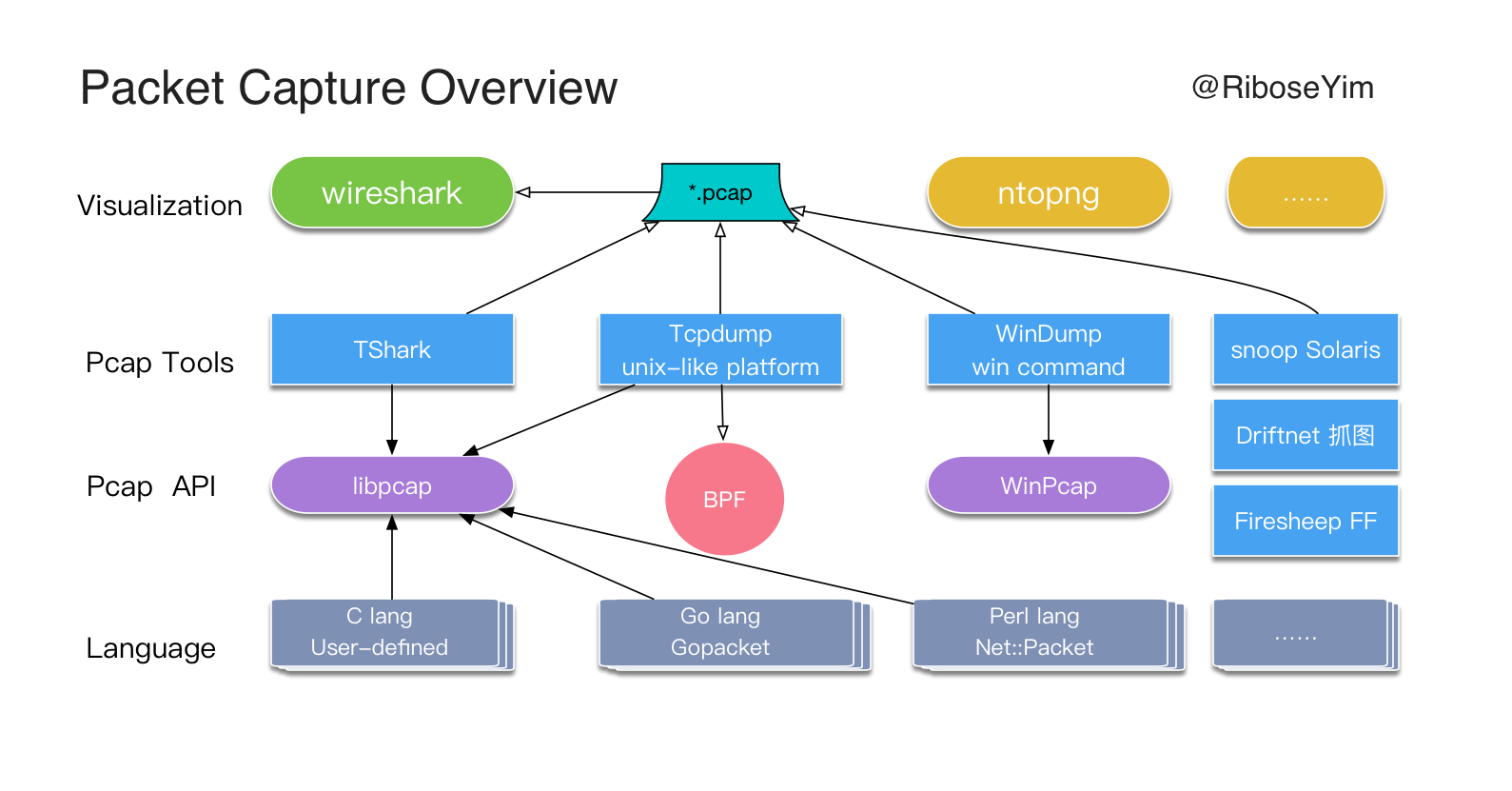
- Packet Capturing Overview
- What is Packet Capturing
- How can it be used
- What is libpcap
- Debug Tools: tcpdump & WinPcap & snoop
- What is BPF
- What is gopacket
What is Packet Capturing
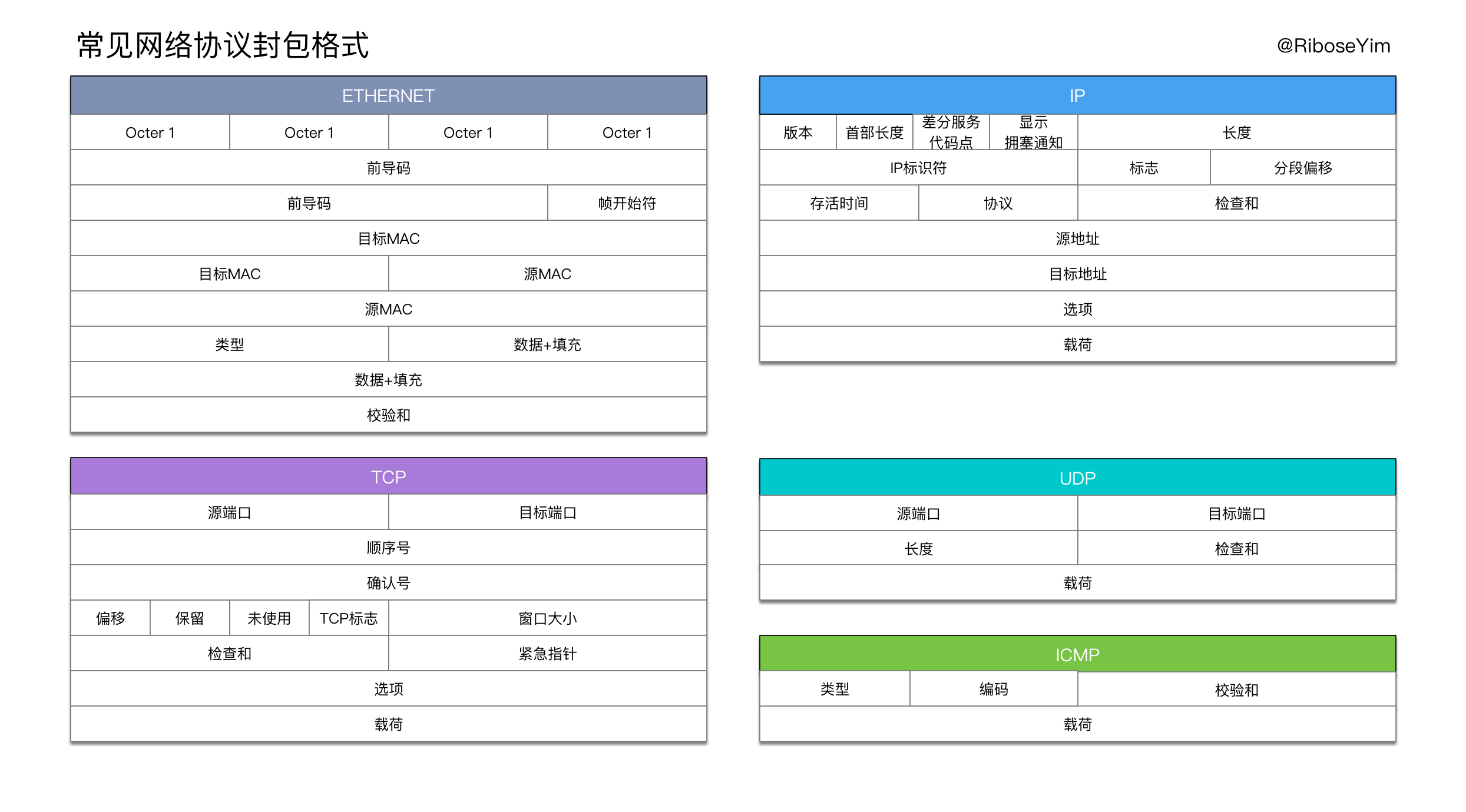
Packet capture is a computer networking term for intercepting a data packet that is crossing or moving over a specific computer network.Once a packet is captured, it is stored temporarily so that it can be analyzed. The packet is inspected to help diagnose and solve network problems and determine whether network security policies are being followed.
How can it be used
Development
Testing & validating & Reverse engineer APP on APINetwork Administration
Seeing what traffic goes on in background,Looking for malicious traffic on networkData capturing is used to identify security flaws and breaches by determining the point of intrusion.Troubleshooting
Managed through data capturing, troubleshooting detects the occurrence of undesired events over a network and helps solve them. If the network administrator has full access to a network resource, he can access it remotely and troubleshoot any issues.Security
defcon Wall of Sheep.Hackers can also use packet capturing techniques to steal data that is being transmitted over a network, like Stealing credentials.When data is stolen, the network administrator can retrieve the stolen or lost information easily using data capturing techniques.Forensics
forensics for crime investigations.Whenever viruses, worms or other intrusions are detected in computers, the network administrator determines the extent of the problem. After initial analysis, she may block some segments and network traffic in order to save historical information and network data.
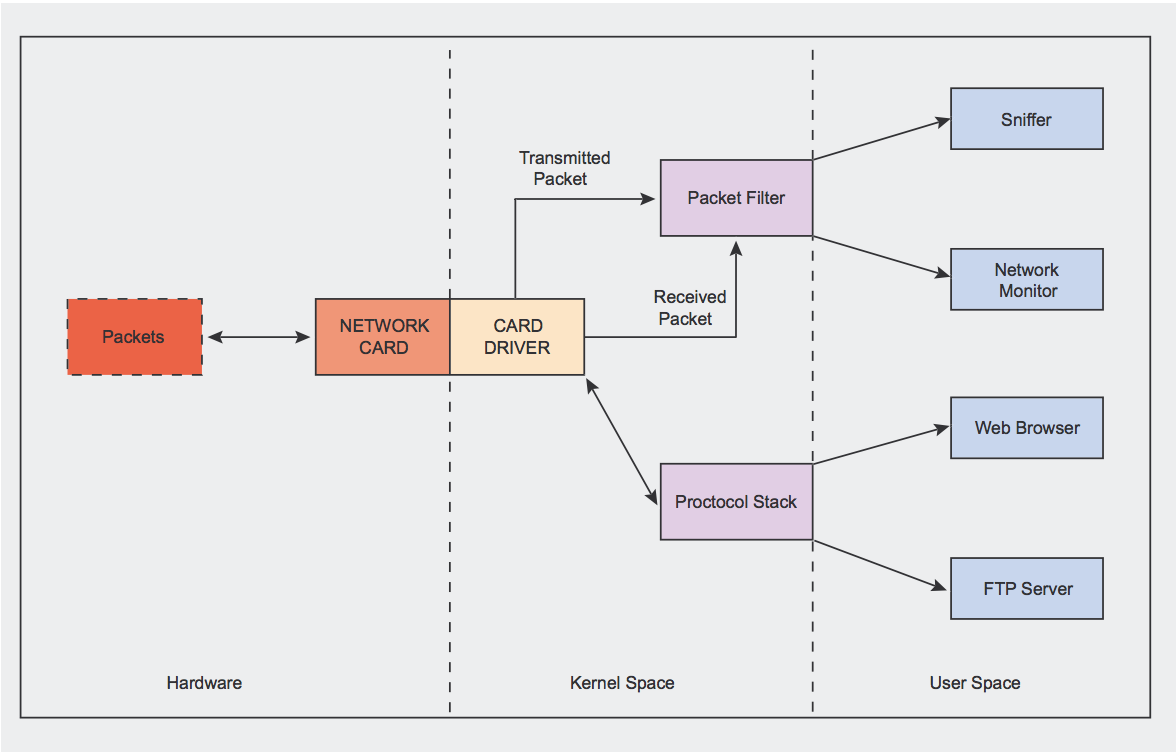
What is libpcap
libpcap flow involving data copy from kernel to user space.
1 | //Compile with: gcc find_device.c -lpcap |
1 |
|
Debug Tools
1 | #Older versions of tcpdump truncate packets to 68 or 96 bytes. |
tcpdump
tcpdump 是一个运行在命令行下的嗅探工具。它允许用户拦截和显示发送或收到过网络连接到该计算机的TCP/IP和其他数据包。它支持针对网络层、协议、主机、网络或端口的过滤,并提供and、or、not等逻辑语句来帮助你去掉无用的信息,从而使用户能够进一步找出问题的根源。可以使用 BPF 来限制tcpdump产生的数据包数量。
snoop
snoop uses both the network packet filter and streams buffer modules to provide efficient capture of packets from the network. Captured packets can be displayed as they are received, or saved to a file for later inspection.
promiscuous mode
抓包工具需要工作在promiscuous mode(混杂模式)(superuser), 指一台机器的网卡能够接收所有经过它的数据流,而不论其目的地址是否是它。当网卡工作在混杂模式下时,网卡将来自接口的所有数据都捕获并交给相应的驱动程序。一般在分析网络数据作为网络故障诊断手段时用到,同时这个模式也被网络黑客利用来作为网络数据窃听的入口。
BPF
Berkeley Packet Filter,缩写BPF,是类Unix系统上数据链路层的一种接口,提供原始链路层封包的收发。BPF支持“过滤”封包,这样BPF会只把“感兴趣”的封包到上层软件,可以避免从操作系统内核向用户态复制其他封包,降低抓包的CPU的负担以及所需的缓冲区空间,从而减少丢包率。BPF的过滤功能是以BPF虚拟机机器语言的解释器的形式实现的,这种语言的程序可以抓取封包数据,对封包中的数据采取算术操作,并将结果与常量或封包中的数据或结果中的测试位比较,根据比较的结果决定接受还是拒绝封包。

Go Packet
Find Devices
1 | package main |
Decoding Packet Layers
1 | package main |
Creating and Sending Packets
1 | package main |
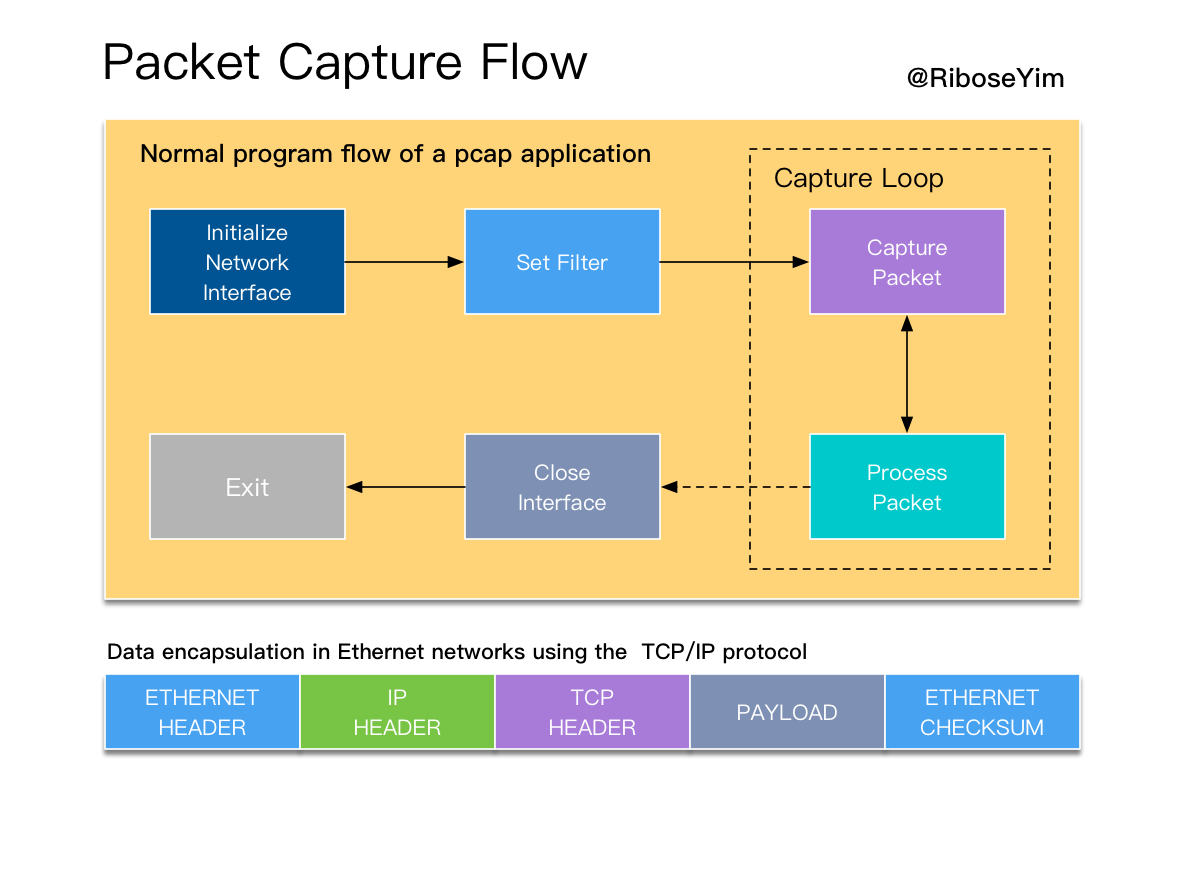
Capture Packet Workflow
- Getting a list of network devices
- Capturing packets from a network device
- Analyzing packet layers
- Using Berkeley Packet Filters
Demo & Repository
Application
- qisniff
- 新一代Ntopng网络流量监控—可视化和架构分析
- ntop:pf_ring
- ntop:pf_ring zero copy
- jaseywang:pf_ring对网络抓包性能的提升
- 胥峰(盛大游戏):网络分析技术之葵花宝典
- 基于网络抓包实现kubernetes中微服务的应用级监控
拓展话题:SDN 网络中的可视化与数据封包
- DPDK(Data Plane Development Kit)
运行于Intel X86平台,是 Intel 开源的一组快速处理数据包的开发平台及接口(BSD)。重载了网卡驱动,该驱动在收到数据包后不中断通知CPU,而是将数据包通过零拷贝技术存入内存,这时应用层程序就可以通过DPDK提供的接口,直接从内存读取数据包。这种处理方式节省了CPU中断时间、内存拷贝时间,并向应用层提供了简单易行且高效的数据包处理方式,使得网络应用的开发更加方便。
专题合辑:Network Engineering
- SDN 技术指南(一): 架构概览
- SDN 技术指南(二):OpenFlow
- Preview SDN 技术指南(三):OpenDaylight or Floodlight ?
- SDN 技术指南(四):Open vSwitch
- Preview SDN 技术指南(五):NFV
- Preview SDN 技术指南(六):OpenStack or Kubernetes ?
- 浅谈基于数据分析的网络态势感知
- 网络数据包的捕获与分析(libpcap、BPF及gopacket)
- 新一代Ntopng网络流量监控—可视化和架构分析
- Cyber-Security: IPv6 & Security
- AWS or Azure : 云计算平台的趋势分析|Stack Overflow,2017
- Cyber-Security|香港警务处网络安全与科技罪案总警司
参考文献
- (推荐)Packet Capture, Injection, and Analysis with Gopacket
- (推荐)The BSD Packet Filter:A New Architecture for User-level Packet Capture
- Programming with Libpcap - Sniffing the Network From Our Own Application
- docs.oracle:Monitoring Packet Transfers With the snoop Command
- MOTS(Man-on-the-Side):一种隐秘的攻击
- (推荐)Deep dive into QUANTUM INSERT
- YouTube:Capturing with Wireshark’s tshark
- Using tshark to Watch and Inspect Network Traffic
- tcpdump:理论、自动抓包及业务架构树的生成

